Define Terraform Providers?
Terraform Providers are plugins that allow Terraform, an infrastructure as code (IaC) tool, to interact with different cloud platforms, services, and APIs. A Terraform Provider acts as a bridge between Terraform and the target infrastructure, enabling users to manage and provision resources in a consistent and automated manner.
Each provider corresponds to a specific cloud provider or service and is responsible for understanding its API, translating Terraform configurations into API requests, and managing the lifecycle of the associated resources. Providers handle tasks such as creating, updating, and deleting resources, as well as retrieving their current state for tracking changes.
Terraform offers a wide range of official providers for popular cloud platforms like Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), and many others. In addition to the official providers, the Terraform community has developed numerous third-party providers for various services, allowing users to manage resources across different cloud environments.
Providers are an essential part of Terraform's flexibility and extensibility, enabling users to define infrastructure configurations using a unified language and apply them across multiple cloud platforms or services.
# Declare the AWS provider and configure credentials
provider "aws" {
region = "us-west-2"
access_key = "YOUR_AWS_ACCESS_KEY"
secret_key = "YOUR_AWS_SECRET_KEY"
}
In this example, the configuration file declares the AWS provider using the provider block. The region specifies the AWS region where the resources will be created, and the access_key and secret_key are the AWS API credentials used for authentication.
Compare the features and supported resources for each cloud platform's Terraform provider to gain a better understanding of their capabilities.
Here's a high-level comparison of the features and supported resources for some of the major cloud platform's Terraform providers:
AWS (Amazon Web Services) Provider:
Features: The AWS provider offers comprehensive support for a wide range of AWS services, including EC2 instances, VPCs, security groups, S3 buckets, RDS databases, IAM roles, Lambda functions, and more. It supports advanced features like AWS CloudFormation integration, resource tagging, and importing existing resources into Terraform state.
Provider Documentation: AWS Provider Documentation
Azure Provider:
Features: The Azure provider enables provisioning and management of Azure resources such as virtual machines, virtual networks, storage accounts, databases, and AKS (Azure Kubernetes Service) clusters. It also supports features like virtual machine scale sets, availability sets, Azure Active Directory integration, and Azure Resource Manager (ARM) templates.
Provider Documentation: Azure Provider Documentation
GCP (Google Cloud Platform) Provider:
Features: The GCP provider supports a wide range of Google Cloud resources, including Compute Engine instances, Cloud Storage buckets, Cloud Functions, Pub/Sub topics, BigQuery datasets, and more. It also offers features like automatic network creation, Cloud IAM integration, and resource import capabilities.
Provider Documentation: GCP Provider Documentation
It's important to note that the capabilities and supported resources of each Terraform provider are continuously evolving, with updates and additions being made by both the cloud providers and the Terraform community. It's recommended to refer to the official provider documentation for the most up-to-date information on features and supported resources.
Explore provider configuration and set up authentication for each provider
Here's an overview of provider configuration and setting up authentication for each of the mentioned Terraform providers:
AWS (Amazon Web Services) Provider:
Provider Configuration: To configure the AWS provider, you need to specify the
providerblock in your Terraform configuration file or use environment variables or shared credentials file. The configuration typically includes theregion,access_key, andsecret_key.Authentication: You can authenticate with AWS using access key and secret key, environment variables, or an AWS shared credentials file. The access key and secret key can be obtained from the AWS Management Console. Alternatively, you can use AWS CLI to configure the credentials.
provider "aws" {
region = "us-west-2"
access_key = "YOUR_AWS_ACCESS_KEY"
secret_key = "YOUR_AWS_SECRET_KEY"
}
You can set the access_key and secret_key directly in the provider block as shown in the configuration example. Alternatively, you can use environment variables (AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY) or a shared credentials file (~/.aws/credentials) to authenticate with AWS.
Azure Provider:
Provider Configuration: To configure the Azure provider, you can either specify the
providerblock in your Terraform configuration file or use environment variables. The configuration typically includes thesubscription_id,client_id,client_secret, andtenant_id.Authentication: You authenticate with Azure using a service principal or managed identity. To create a service principal, you can use the Azure CLI or Azure Portal. The client ID, client secret, and tenant ID associated with the service principal are used for authentication.
provider "azurerm" {
subscription_id = "YOUR_AZURE_SUBSCRIPTION_ID"
client_id = "YOUR_AZURE_CLIENT_ID"
client_secret = "YOUR_AZURE_CLIENT_SECRET"
tenant_id = "YOUR_AZURE_TENANT_ID"
}
You can obtain the subscription_id, client_id, client_secret, and tenant_id from the Azure Portal or using the Azure CLI. Set these values in the provider block as shown in the configuration example.
These are general guidelines for setting up authentication for each provider. It's important to refer to the provider documentation for specific details and any additional configuration options that may be required for advanced authentication scenarios or specific use cases.
Practice Using Providers
Choose a cloud platform (AWS, Azure, Google Cloud, or others) as your target provider for this task.
Create a Terraform configuration file named
main.tfand configure the chosen provider within it.Authenticate with the chosen cloud platform using the appropriate authentication method (e.g., access keys, service principals, or application default credentials).
Deploy a simple resource using the chosen provider. For example, if using AWS, you could provision a Virtual Private Cloud (VPC), Subnet Group, Route Table, Internet Gateway, or a virtual machine.
Step 1:- first we need to create provider
provider "aws" {
region = "us-east-1"
}
Step 2:-VPC Creation: Define a VPC configuration in Terraform. Here's an example:
resource "aws_vpc" "my_vpc" {
cidr_block = "10.0.0.0/16"
tags = {
Name = "MyVPC"
}
}
This creates a VPC with the CIDR block 10.0.0.0/16 and assigns the name tag "MyVPC" to it.
Step 3:- Subnet Group: Create a subnet within the VPC. Here's an example:
resource "aws_subnet" "my_subnet" {
vpc_id = aws_vpc.my_vpc.id
cidr_block = "10.0.0.0/24"
availability_zone = "us-east-1a"
map_public_ip_on_launch = true
tags = {
Name = "MySubnet"
}
}
In this example, a subnet is created with the CIDR block 10.0.0.0/24 within the VPC. It's associated with the availability zone us-east-1a, and the map_public_ip_on_launch attribute is set to true, allowing instances in this subnet to have public IP addresses.
Step 4:- Route Table and Internet Gateway: Create a route table and associate it with the VPC. Also, create an internet gateway and attach it to the VPC. Here's an example:
resource "aws_route_table" "my_route_table" {
vpc_id = aws_vpc.my_vpc.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.my_internet_gateway.id
}
tags = {
Name = "MyRouteTable"
}
}
resource "aws_internet_gateway" "my_internet_gateway" {
vpc_id = aws_vpc.my_vpc.id
tags = {
Name = "MyInternetGateway"
}
}
In this example, a route table is created and associated with the VPC. A route is defined to route traffic with the CIDR block 0.0.0.0/0 (all traffic) through the internet gateway, which is also created and attached to the VPC.
Step 5:- Virtual Machine: Finally, create a virtual machine (EC2 instance) within the subnet. Here's an example:
resource "aws_instance" "my_instance" {
ami = "ami-0123456789abcdef0"
instance_type = "t2.micro"
subnet_id = aws_subnet.my_subnet.id
key_name = "my_key_pair"
tags = {
Name = "MyInstance"
}
}
In this example, an EC2 instance is created with the specified AMI ID, instance type, subnet ID, and key pair. The tags block assigns a name tag to the instance.
Remember to replace the placeholder values (ami-0123456789abcdef0, my_key_pair, etc.) with the appropriate values for your setup.
These are basic examples to get you started. You can further customize the configurations based on your requirements and additional resources you want to create within the VPC.
Once you have defined the Terraform configuration in a .tf file, you can run terraform init to initialize the working directory, terraform plan
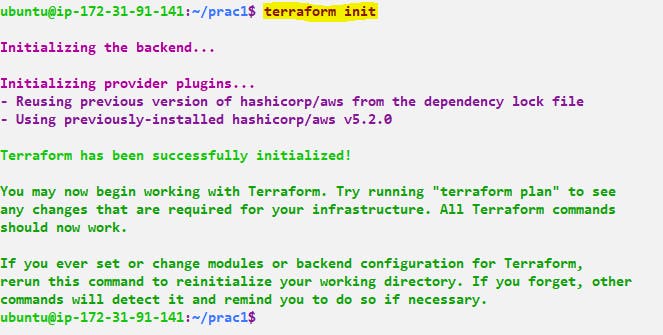
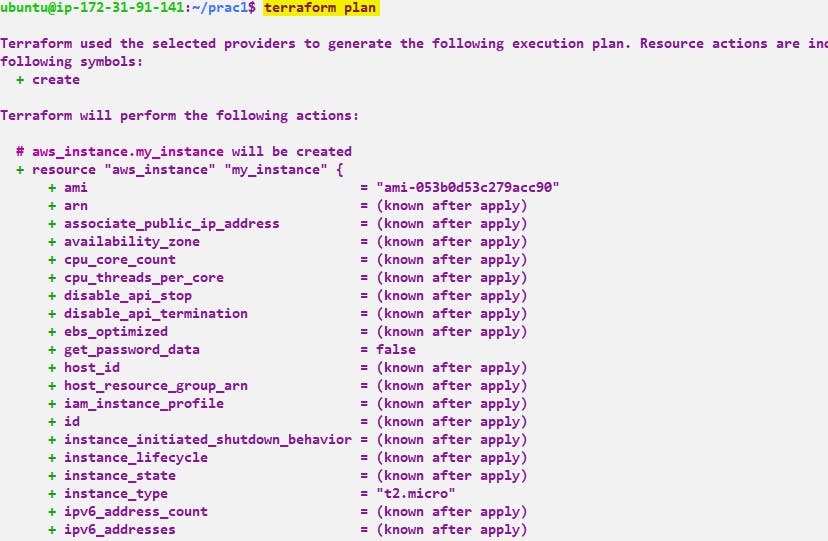
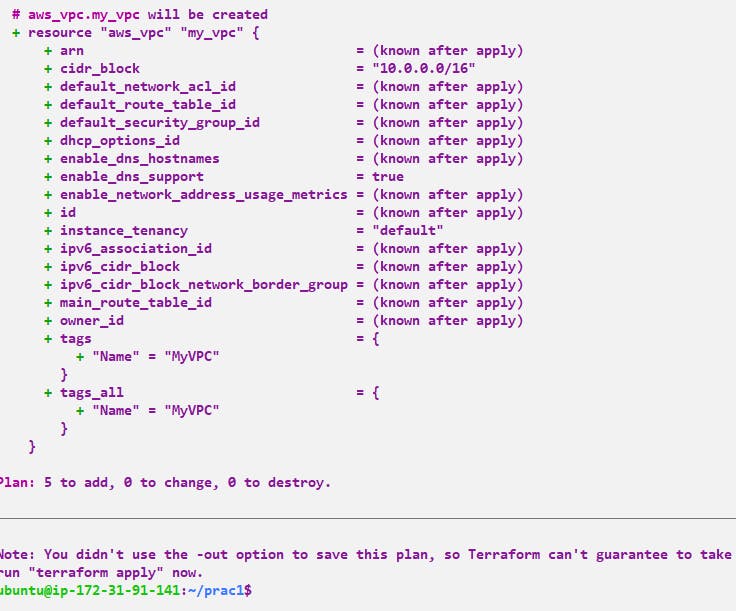
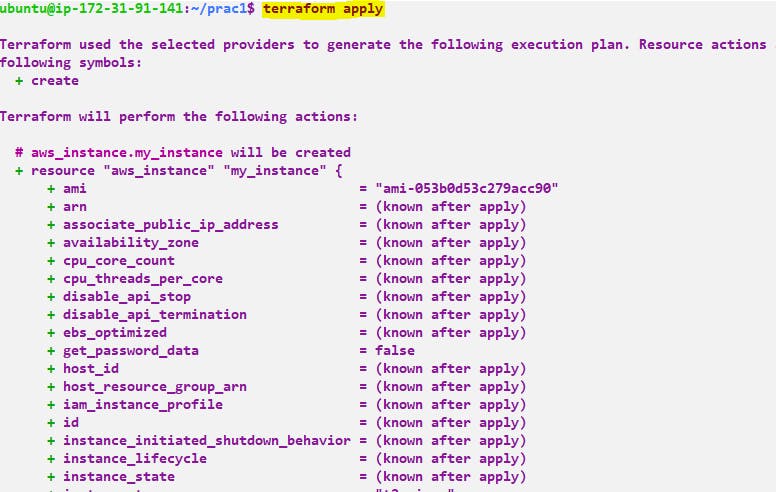
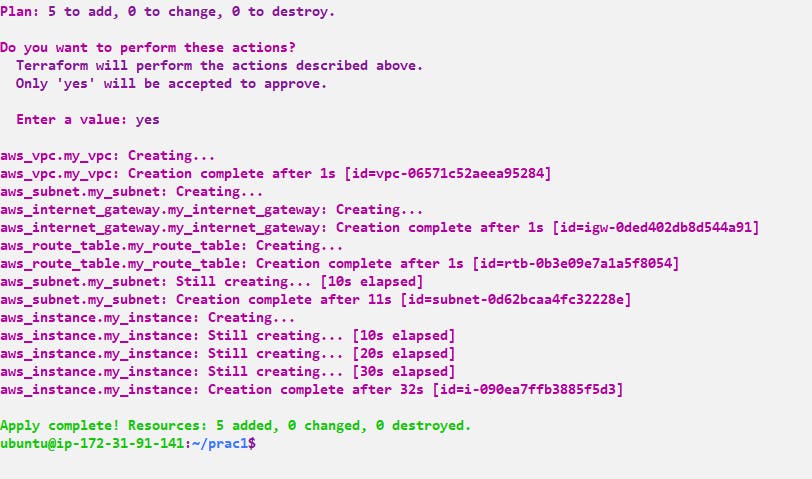
Step 6:- Now we need to check whether it's created or not
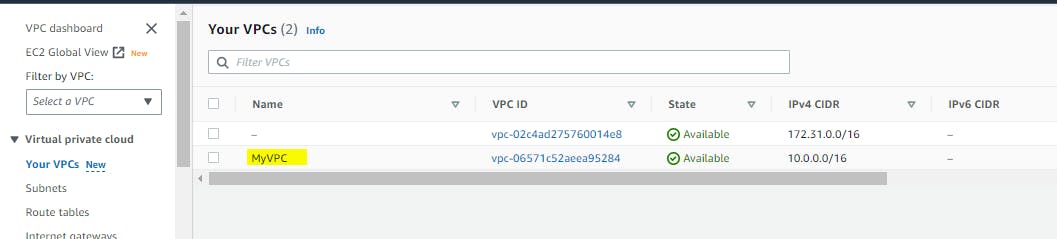
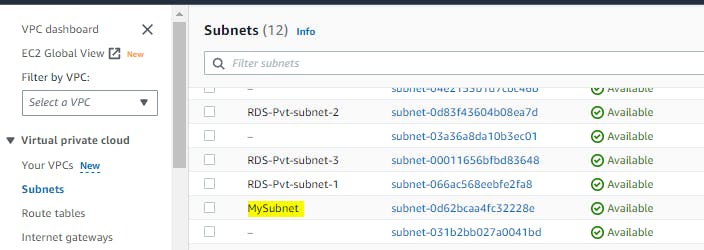
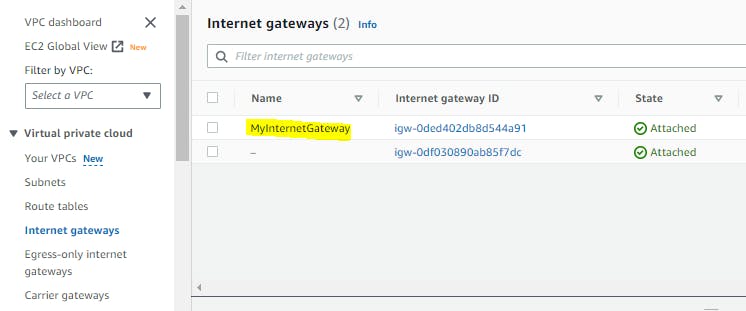
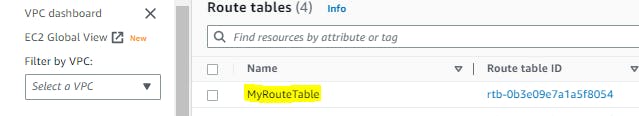
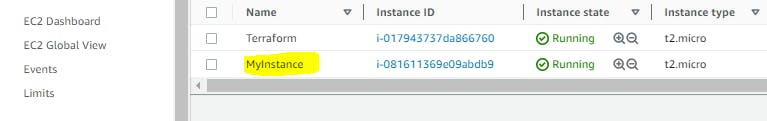
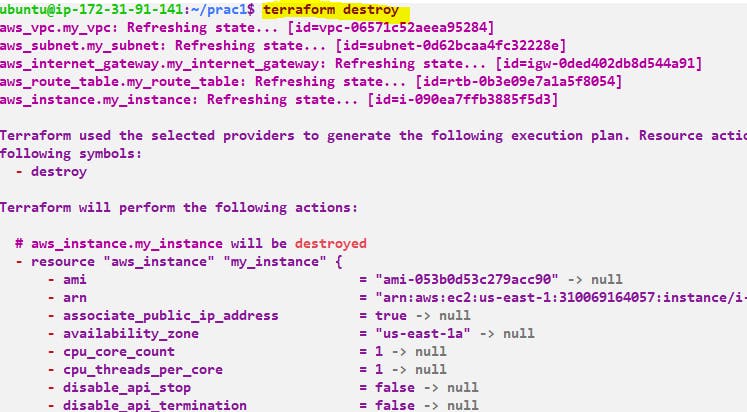
Step 7:- terraform destroy - command is used to destroy the infrastructure and resources managed by Terraform. It removes all the resources defined in your Terraform configuration files and deletes them from the target cloud platform
Thank you for reading!! I hope you find this article helpful!!
if any queries or corrections to be done to this blog please let me know.
Happy Learning!!
Saikat Mukherjee

